Magnet Forensics have announced a weekly CTF running from October 2020. A new challenge will be released each week on Monday, and the first few are based on an Android filesystem dump.
MD5: 3bb6abb3bf6d09e3e65d20efc7ec23b1 SHA1: 10cc6d43edae77e7a85b77b46a294fc8a05e731d
Let’s go!
Mapping the Digits (20 points)
What time was the file that maps names to IP’s recently accessed?
(Please answer in this format in UTC: mm/dd/yyyy HH:MM:SS)
A pretty simple one to start with. On Linux-based systems (like Android) hostnames are mapped to IP addresses in the /etc/hosts file; find that file in the TAR archive and check the timestamp.
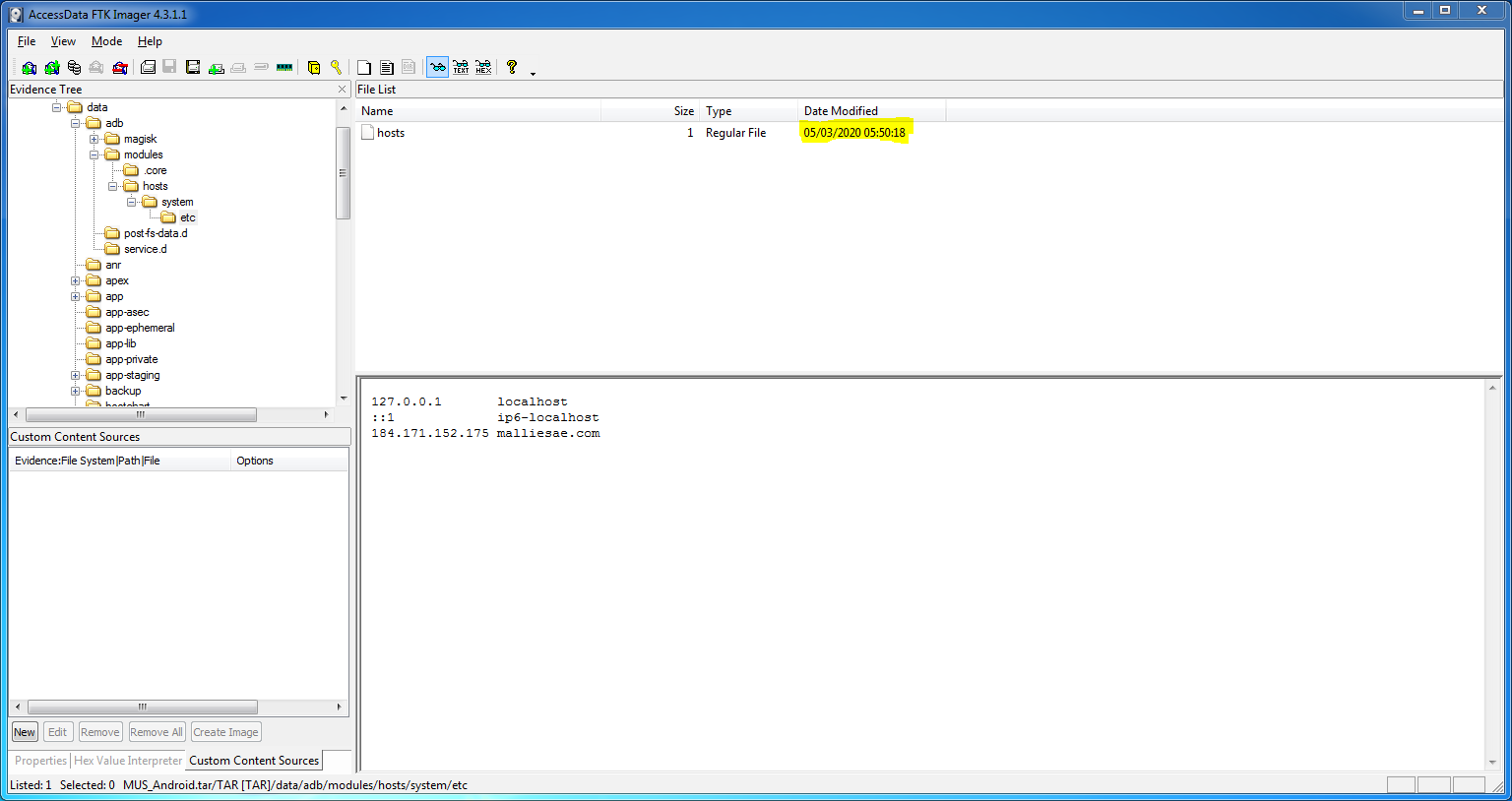
I opened the TAR archive up using FTK Imager, and navigated to the directory containing the hosts file:
/data/adb/modules/hosts/system/etc
There is only one timestamp, but it is worth noting that I have FTK Imager set to display dates in the common European format (day/month/year):
05/03/2020 05:50:18
So swap the day and month values to match the US format required by the question, and we have our first answer.
Flag
03/05/2020 05:50:18
As an aside, confusion around date and timestamps is exactly why we have ISO 8601.
1 thoughts on “Magnet Weekly CTF – Week 1 – Mapping the Digits”