The Magnet Forensics Weekly CTF has been running since October and sets one question each week using an image that changes each month. The October questions were based on an Android filesystem dump, and November’s related to a compromised Hadoop cluster built on Ubuntu Linux. The December challenges return to more familiar territory for me – Windows memory analysis!
These questions use the memory image from the Magnet Virtual Summit 2020, which I first examined during the MVS CTF earlier this year. You can find the rest of my Magnet Weekly CTF write-ups here.
Week 10 is another multi-part question and was set by Jamey Tubbs. This write-up follows on from Week 9 where I made a point of saving my Volatility output for later reference, so you might want to read my Week 9 write-up to see how I approached the initial stages of the analysis.
Part 1 (15 Points)
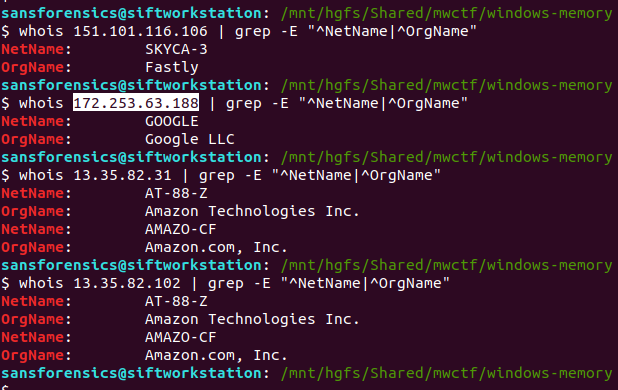
At the time of the RAM collection (20-Apr-20 23:23:26- Imageinfo) there was an established connection to a Google Server.
What was the Remote IP address and port number? format: “xxx.xxx.xx.xxx:xxx”
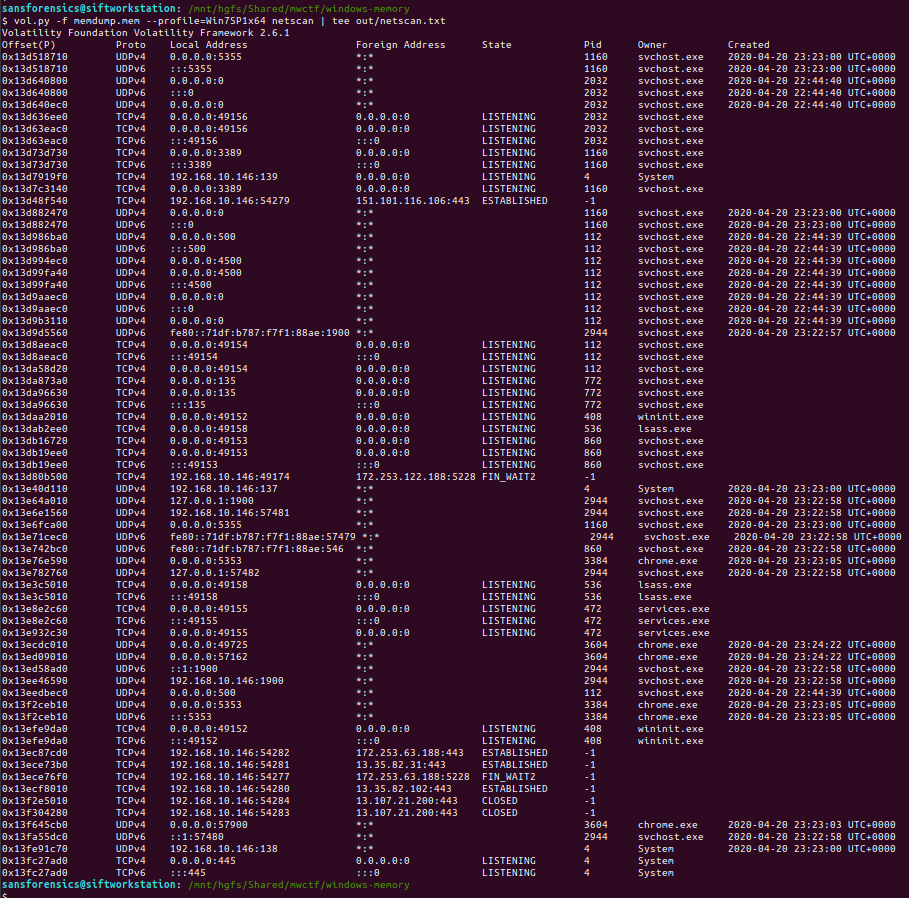
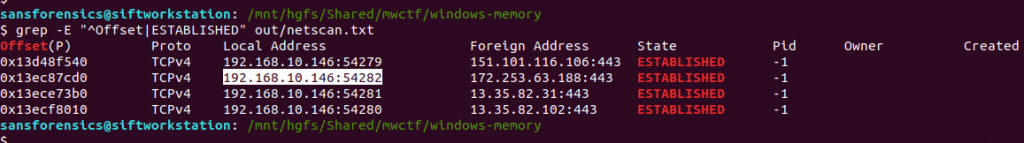
We want to examine the network connections that were active at the time the memory dump was captured; the netscan plugin will dump these out for us.
vol.py -f memdump.mem --profile=Win7SP1x64 netscan | tee out/netscan.txt
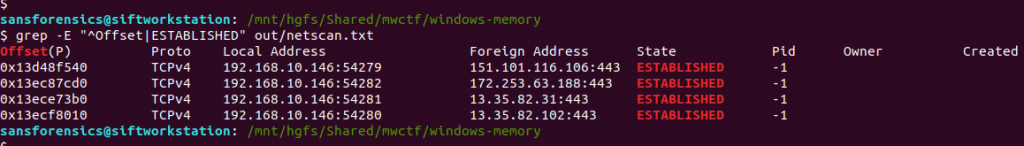
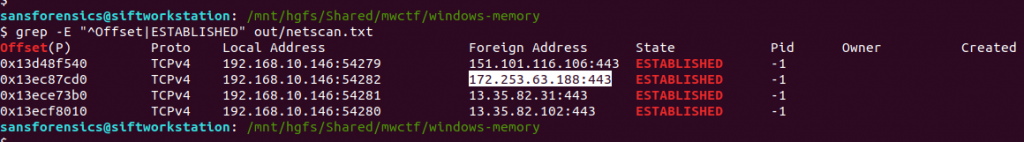
We are looking specifically for established connections, which can be filtered from the saved output using grep:
grep -E "^Offset|ESTABLISHED" out/netscan.txt
Unfortunately we don’t have any timestamps associated with these connections yet, but using whois it is a simple task to determine which of the four IP addresses belongs to Google:
whois 151.101.116.106 | grep -E "^NetName|^OrgName" whois 172.253.63.188 | grep -E "^NetName|^OrgName" whois 13.35.82.31 | grep -E "^NetName|^OrgName" whois 13.35.82.102 | grep -E "^NetName|^OrgName"
The question asks us to supply the IP address and port number, so back to our list of established connections and submit both as the answer to Part 1.
Flag (Part 1)
172.253.63.188:443
Part 2 (15 points)
What was the Local IP address and port number?
We already know this from our work to answer Part 1.
Flag (Part 2)
192.168.10.146:54282
Part 3 (10 points)
What was the URL?
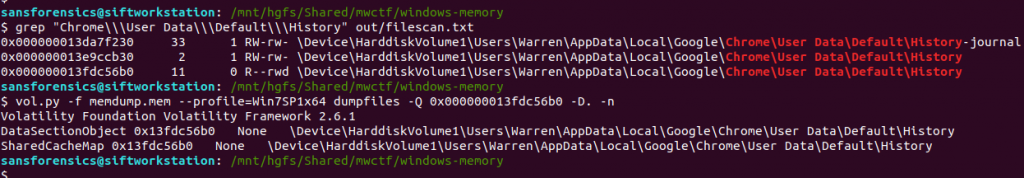
This part wasn’t so obvious initially. I tried running strings and Volatility’s yarascan plugin looking for any references to the IP address, but did not find anything useful. After looking at the running processes again (saved pstree output) I extracted the Google Chrome browser history…
grep "Chrome\\\User Data\\\Default\\\History" out/filescan.txt vol.py -f memdump.mem --profile=Win7SP1x64 dumpfiles -Q 0x000000013fdc56b0 -D. -n
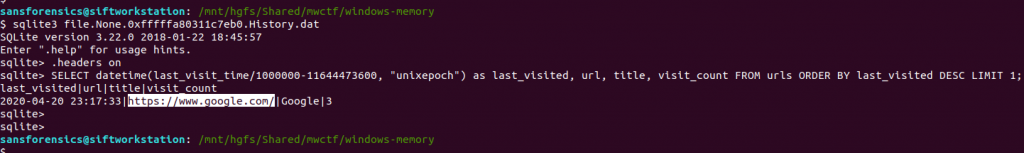
…and examined the urls table using sqlite3:
sqlite3 file.None.0xfffffa80311c7eb0.History.dat sqlite> .headers on sqlite> SELECT datetime(last_visit_time/1000000-11644473600, "unixepoch") as last_visited, url, title, visit_count FROM urls ORDER BY last_visited DESC LIMIT 1;
The timestamp of the most recently visited URL doesn’t match the time of the memory capture exactly, but it is close enough to be worth submitting.
Flag (Part 3)
https://www.google.com
Part 4 (5 points)
What user was responsible for this activity based on the profile?
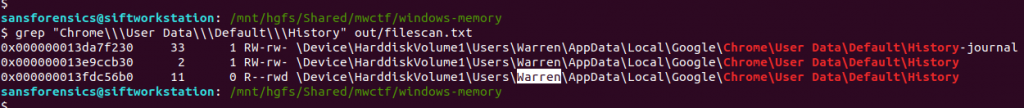
Again, we already know the answer to this one based on Part 3, where we extracted the Google Chrome history database from Warren’s user profile.
Flag (Part 4)
Warren
Part 5 (20 points)
How long was this user looking at this browser with this version of Chrome? *format: X:XX:XX.XXXXX * Hint: down to the last second
Now this is the part that caused the most trouble! Part 5 was initially worth 10 points, but later in the week it was assigned an extra 10 points, and a hint was added which could be unlocked by spending some points. In the end, this question was actually pretty simple. I spent more time trying to work out what the question was asking than actually solving it!
We are looking for some record of application execution, and after consulting the SANS Windows Forensic Analysis poster I realised that the UserAssist registry keys would likely hold the answer. The UserAssist keys are held in the user’s ntuser.dat hive, and for reasons only apparent to Microsoft, are ROT13 encoded. As I was mentally preparing myself to extract and decode all these GUIDs I looked again at the list of plugins shipped with Volatility on my SIFT VM, and found Jamie Levy’s amazing userassist plugin!
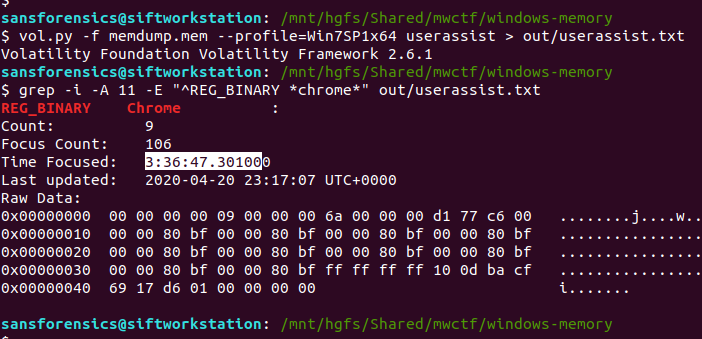
The userassist plugin produces a lot of output! As usual I redirected this to a file, and used grep to find any data relating to Google Chrome.
vol.py -f memdump.mem --profile=Win7SP1x64 userassist > out/userassist.txt grep -i -A 11 -E "^REG_BINARY *chrome*" out/userassist.txt
The value we are interested in is Time Focused, which tracks the length of time that a GUI application was active on the screen.
At this point I was pretty sure I had the challenge solved for the week, but my answer of 3:36:47.301000 was rejected. What else could it be? I looked at the question again and counted the length of the formatting hint – my answer was one digit too long. I dropped the trailing 0, and my answer was accepted.
Flag (Part 5)
3:36:47.30100