In January 2021 Crowdstrike opened up their AdversaryQuest CTF. The CTF consisted of 12 challenges split across three new “threat actors”: SPACE JACKAL, PROTECTIVE PENGUIN, and CATAPULT SPIDER. The challenges mostly focused on binary exploitation and reverse engineering which is a bit of a departure from my skillset. Nonetheless I was able to solve two of the twelve challenges; this one relating to the SPACE JACKAL adversary, and another from CATAPULT SPIDER.
Not to be confused with spaceflight enthusiasts, SPACE JACKAL have very strict opinions on source code indentation. Brought together by their unbounded hate for ASCII character 9, they will not rest until the last tab stop has been eradicated from the face of the Internet.
The Proclamation
A mysterious file appeared on a deep dark web forum. Can you figure out what we can’t see right now?
NOTE: Flags will be easily identifiable by following the format CS{some_secret_flag_text}. They must be submitted in full, including the CS{ and } parts.
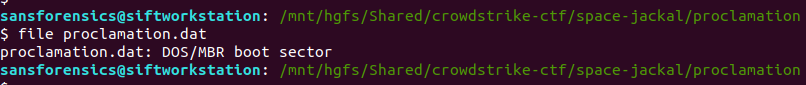
We are given a 512 byte file proclamation.dat and left to get on with it. The first thing I did was use the file utility to determine what kind of data we are dealing with.
file proclamation.dat
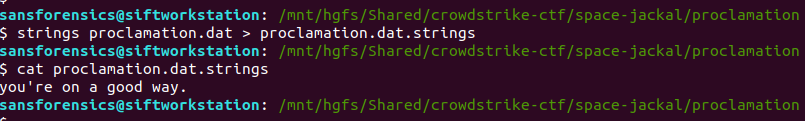
The file is identified as a DOS/MBR boot sector. Interesting. Let’s see what strings gives us.
strings proclamation.dat > proclamation.dat.strings cat proclamation.dat.strings
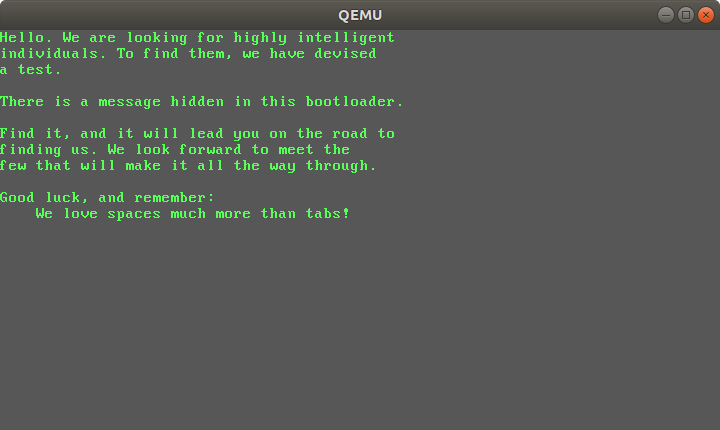
Ok. After a bit of digging on Google I was able to boot the file using the qemu emulation platform.
qemu-system-i386 proclamation.dat
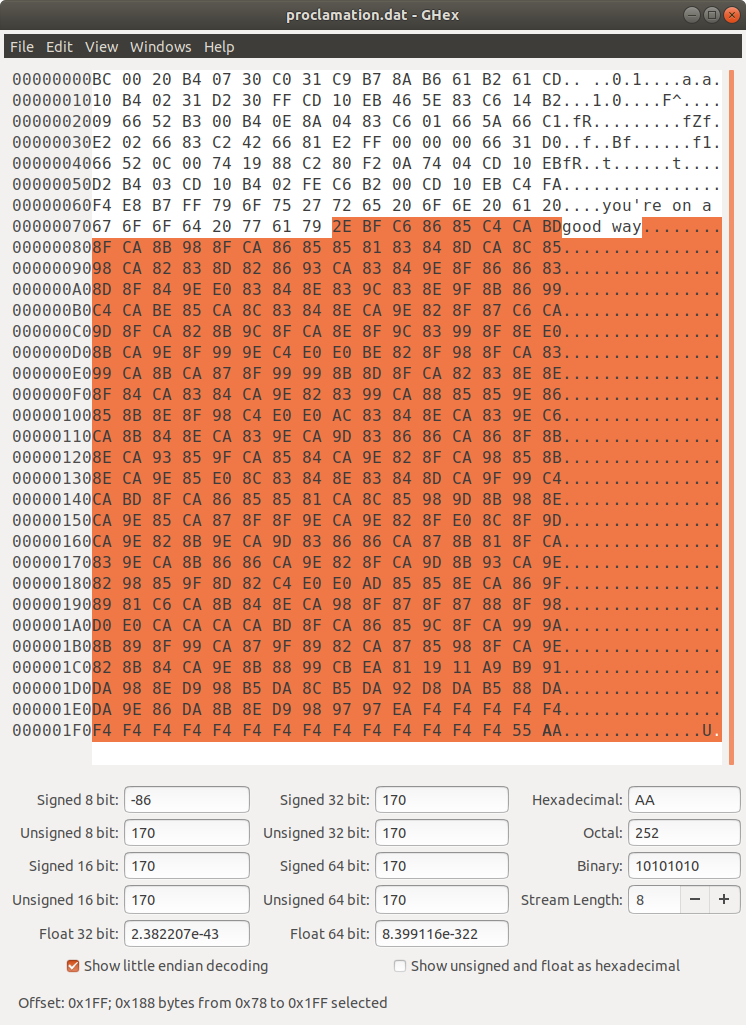
Cool! Now what? Examining the file in a hex editor showed what looked like random data; maybe it is encrypted somehow?
I wasn’t really sure how to proceed with this – encryption and reverse engineering aren’t my usual thing – but I do know CyberChef! I have an instance of CyberChef installed locally on my SIFT VM so I used that instead of the hosted instance, but the process is the same.
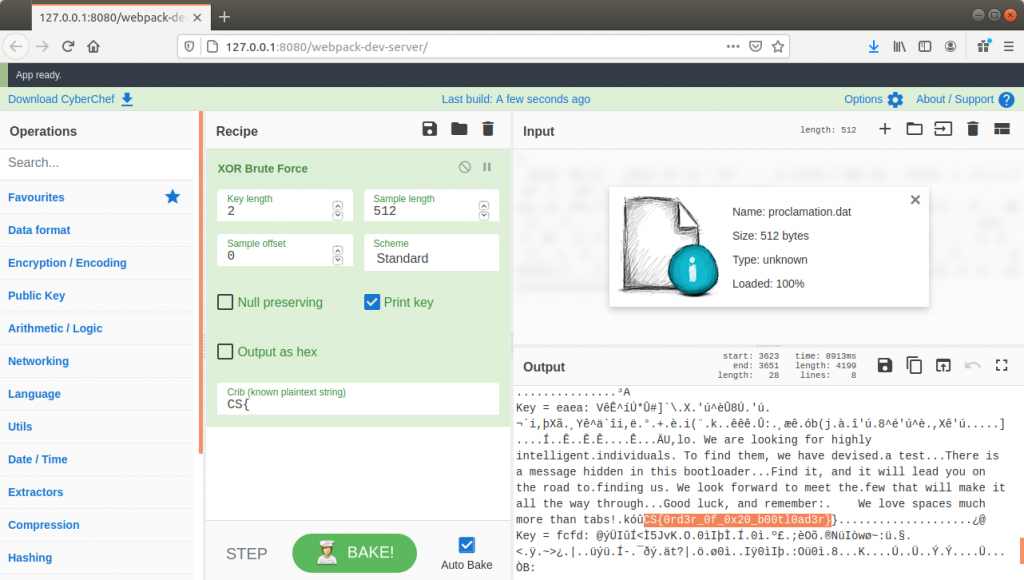
Assuming that the random data was actually encrypted, my first guess was to use the XOR Brute Force operation with a Key Length of 1, but that didn’t output anything intelligible. Next I tried increasing the Key Length to 2 and, in an attempt to cut down on the output, set the flag format – CS{ – as a crib.
CyberChef chewed on this for a minute or so then popped out eight potential decryptions. Examining the output for Key = eaea, I found the same text that was displayed when I used qemu to run the file, and then, appended to the end of the text, the flag!
Flag
CS{0rd3r_0f_0x20_b00tl0ad3r}

1 thoughts on “Crowdstrike AdversaryQuest CTF – The Proclamation”