In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. This series of write-ups covers the network forensics section. As the questions were split over multiple PCAP files (shell, smb, dhcp, network, dns, and https), I have decided to split my write-ups by PCAP for ease of reading.
This write-up covers the questions relating to the dns PCAP file.
MD5: 8663f79d064047f32c9d90791316fce1 SHA1: bda5cafbce553fc6c6fad6b5c300ed65570be2fb
01 – Some good ol fashion txt (50 points)
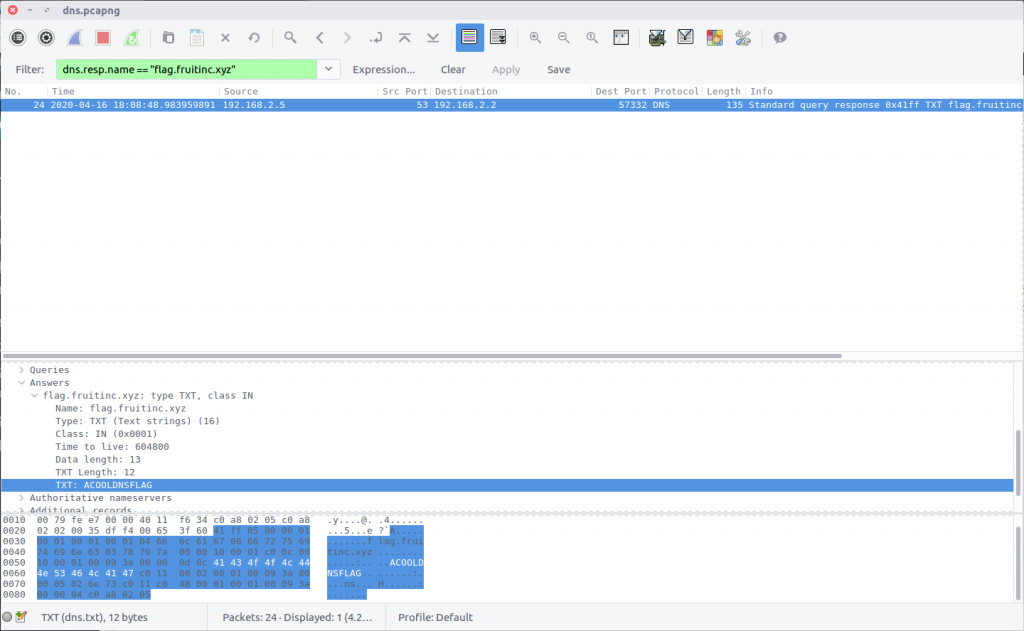
What is the response for the lookup for flag.fruitinc.xyz?
Wireshark has a comprehensive list of built-in Display Filters for working with DNS traffic. In this case we can use the following filter to isolate packets relating to the DNS response to queries for the specified domain:
dns.resp.name == "flag.fruitinc.xyz"
Examining the Answers section of the Packet Details we find a TXT record containing the flag.
flag<ACOOLDNSFLAG>
02 – I have the answers (75 points)
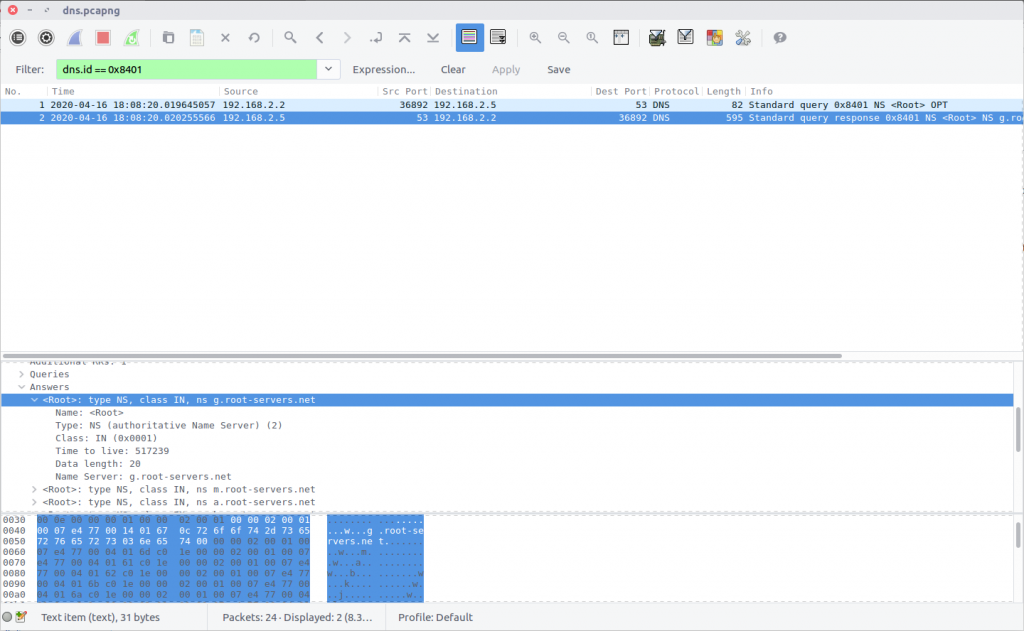
Which root server responds to the query?
Format: flag<hostname>
This question is relatively simple but required some digging through the PCAP to answer. The first DNS response in the PCAP contains a list of the DNS Root Servers.
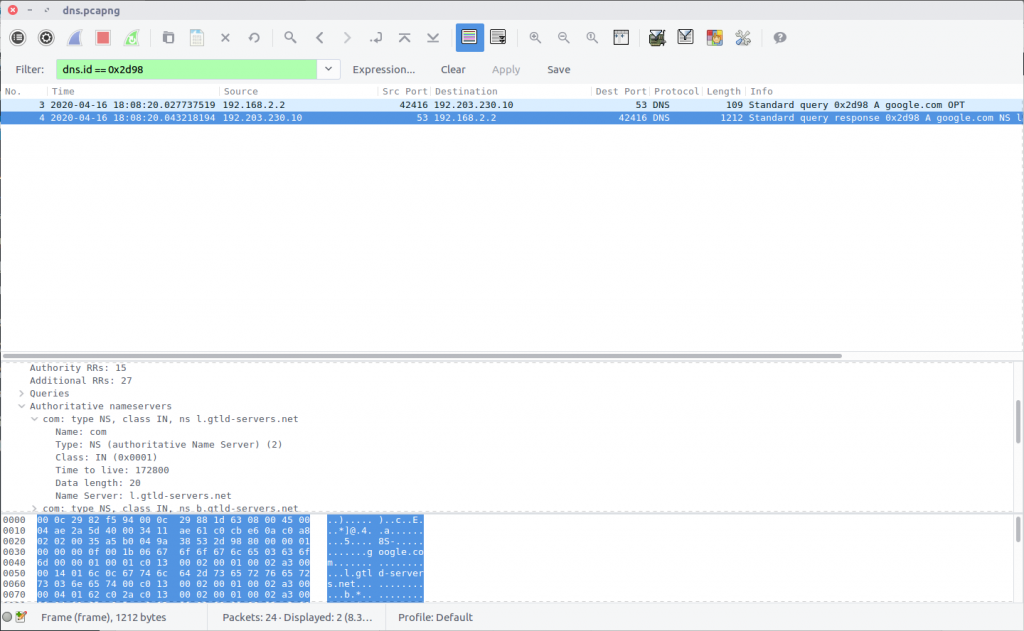
In the next request, the Root Server is queried for the relevant Top Level Domain DNS server. Following that, a request is made to the TLD Server for the Authoritative Name Server, and then ultimately for the domain itself. We need to determine which Root Server responded during this sequence.
Checking the IP address of the Root Server, we find that our query was answered by 192.203.230.10, which has the hostname e.root-servers.net.
flag<e.root-servers.net>
4 thoughts on “DFA/CCSC Spring 2020 CTF – Wireshark – dns.pcapng Write-up”