In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. This series of write-ups covers the network forensics section. As the questions were split over multiple PCAP files (shell, smb, dhcp, network, dns, and https), I have decided to split my write-ups by PCAP for ease of reading.
This write-up covers the questions relating to the https PCAP file.
MD5: c634a81223887075a4972e086e6849c4 SHA1: 5df0d28254eae799634d37d81b78f6c148c5f573
01 – Some secret sauce (200 points)
What has been added to web interaction with web01.fruitinc.xyz?
Before we can start answering questions we need to decrypt the encrypted traffic. Wireshark allows us to decrypt TLS traffic by supplying the Pre-Master Secret helpfully provided in the secret-sauce.txt file that was included with the challenge PCAPs.
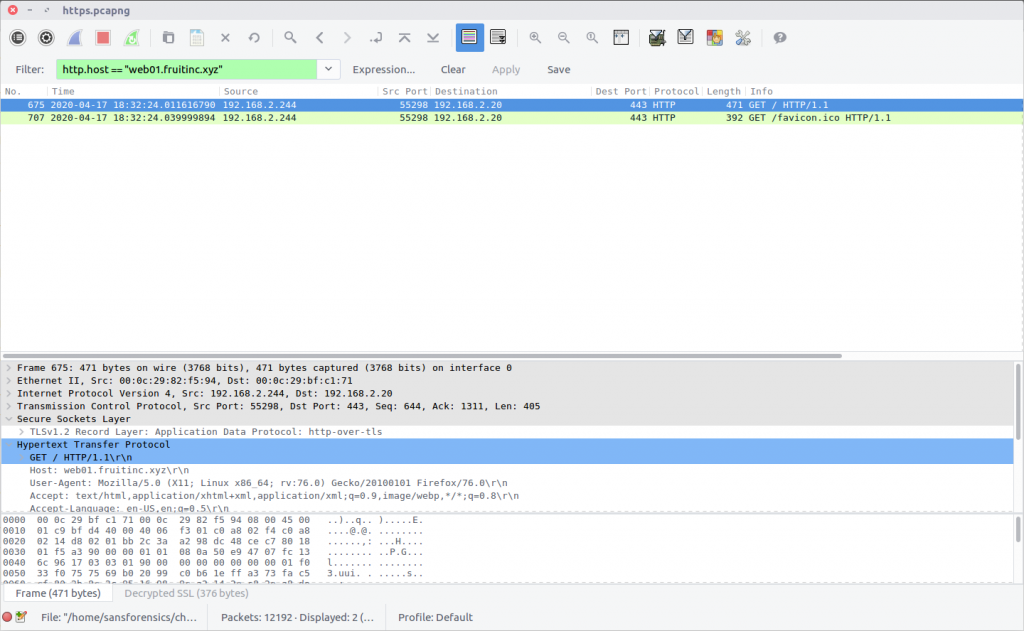
After decrypting the traffic we can filter for traffic to the web server in question:
http.host == "web01.fruitinc.xyz"
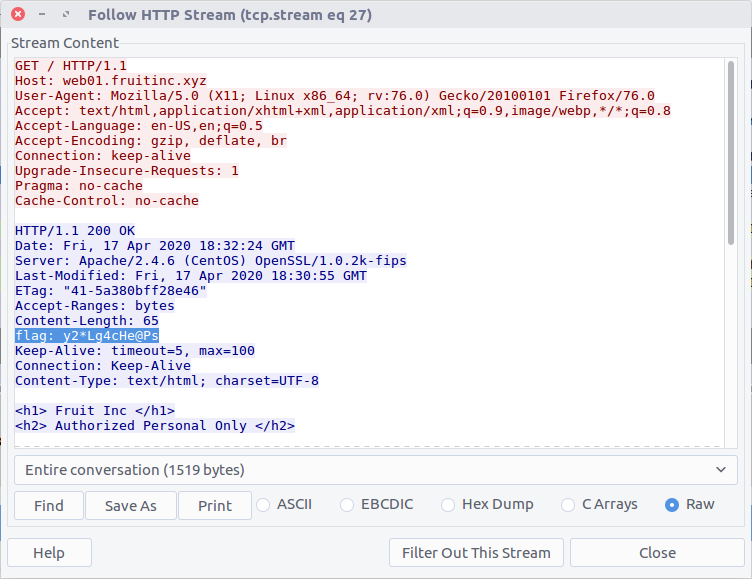
This filter only shows us packets specifically containing the HTTP request headers, but by selecting the Follow HTTP Stream option (Stream #27) we can more easily read the exchange between the client and server, including the flag inserted into the server response headers.
flag<y2*Lg4cHe@Ps>
02 – A sneak peak (300 points)
What is the name of the photo that is viewed in slack?
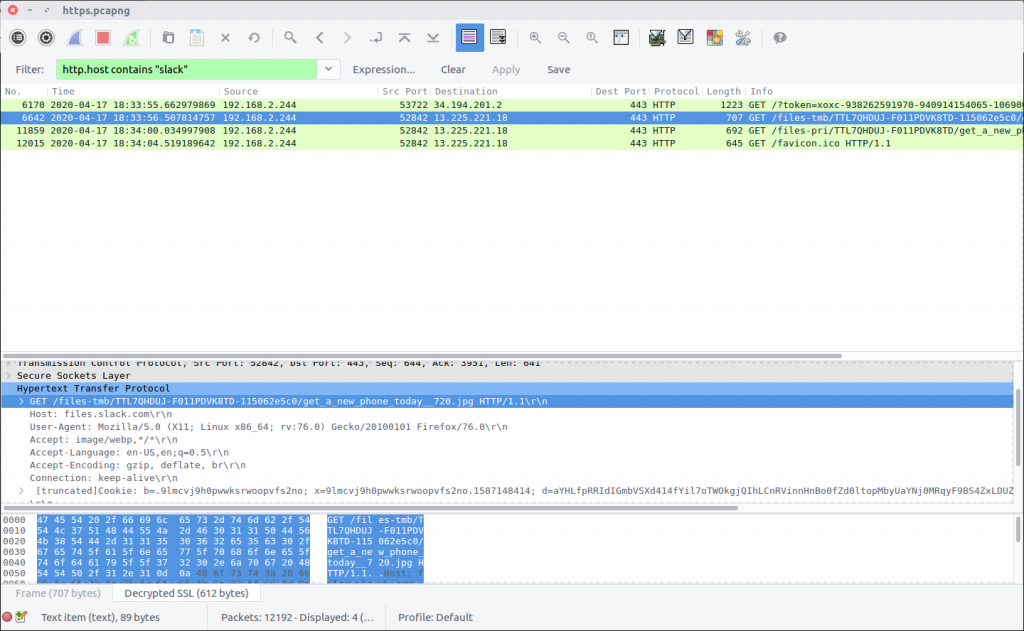
I’m not familiar with how Slack operates on the network level, but checking for HTTP requests containing “slack” in the host header field seemed a sensible start.
http.host contains "slack"
There are two GET requests referring to JPEG files, entering the first one gives our flag. Out of curiosity I also exported the image using the Export Objects function, which would also have shown the filenames.
flag<get_a_new_phone_today__720.jpg>
03 – Someone needs a change (400 points)
What is the email of someone who needs to change their password?
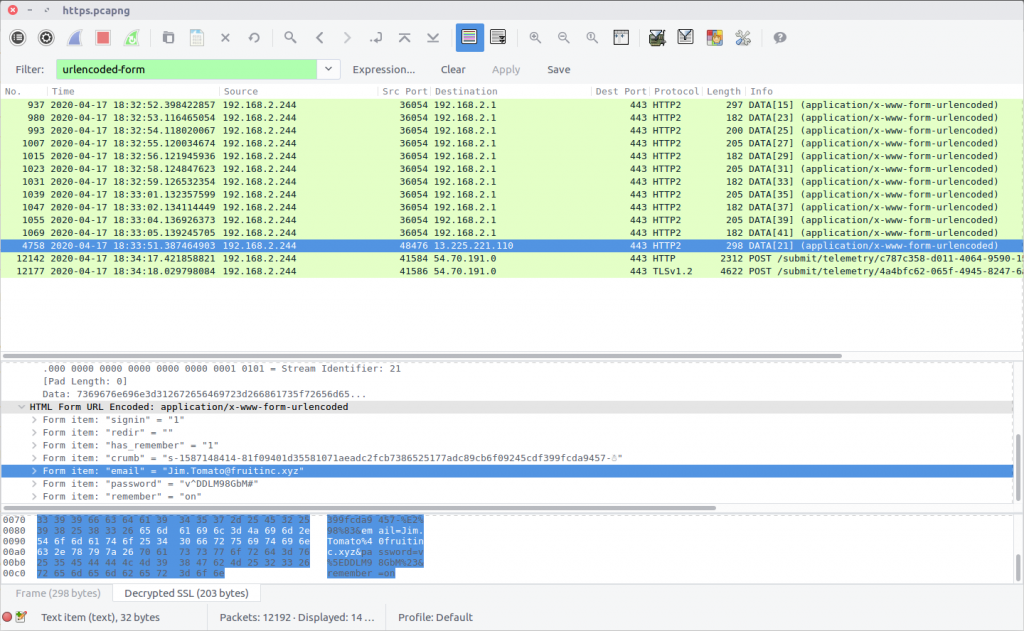
I actually found the answer to this question by chance while working on Question 4. I while reviewing the HTTP2 traffic I noticed one transfer of urlencoded-form data going to a different server; examining the packet (Frame #4758) I found the user details.
urlencoded-form
flag<Jim.Tomato@fruitinc.xyz>
04 – That’s not good (400 points)
What is the username and password to login to fw01.fruitinc.xyz?
Format flag<username:password>
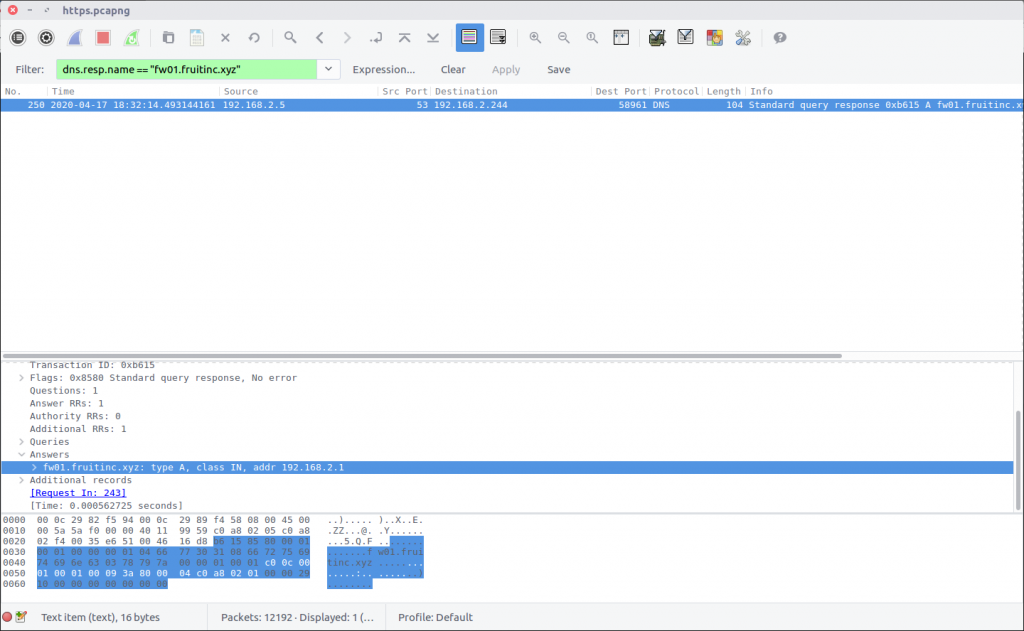
I prefer to use Wireshark with the DNS resolution option disabled, so my first task for this question was to confirm the IP address of the host. There are a few ways of doing this; I first checked for DNS responses:
dns.resp.name == "fw01.fruitinc.xyz"
After confirming the host IP address I started filtering its traffic. There was no HTTP traffic; instead we are looking at HTTP2 which complicated things slightly. Not being familiar with HTTP2 I ended up examining the exchanges between the client and server manually, accidentally answering Question 3 in the process!
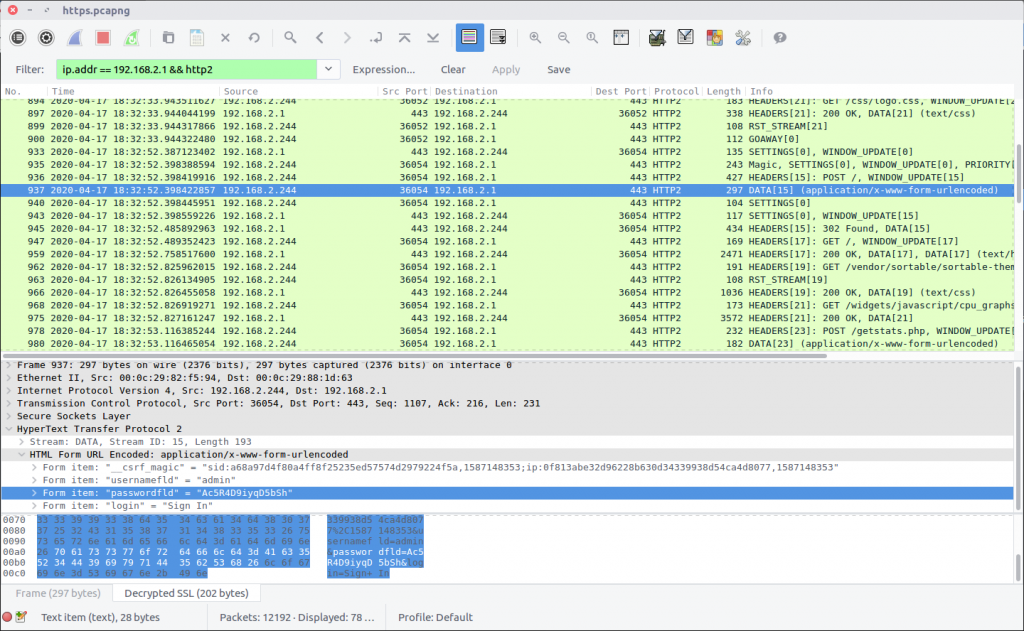
ip.addr == 192.168.2.1 && http2
After some digging I realised that the actual content of the POST request was contained in the DATA packet following the request HEADERS; in this case Frame #937 contained the login details.
flag<admin:Ac5R4D9iyqD5bSh>
05 – What changed? (600 points)
A service is assigned to an interface. What is the interface and what is the service?
Format: flag<interface:service>
There was nothing very elegant about the way I solved this question! Filtering the HTTP2 traffic in the same way as in the previous question:
ip.addr == 192.168.2.1 && http2
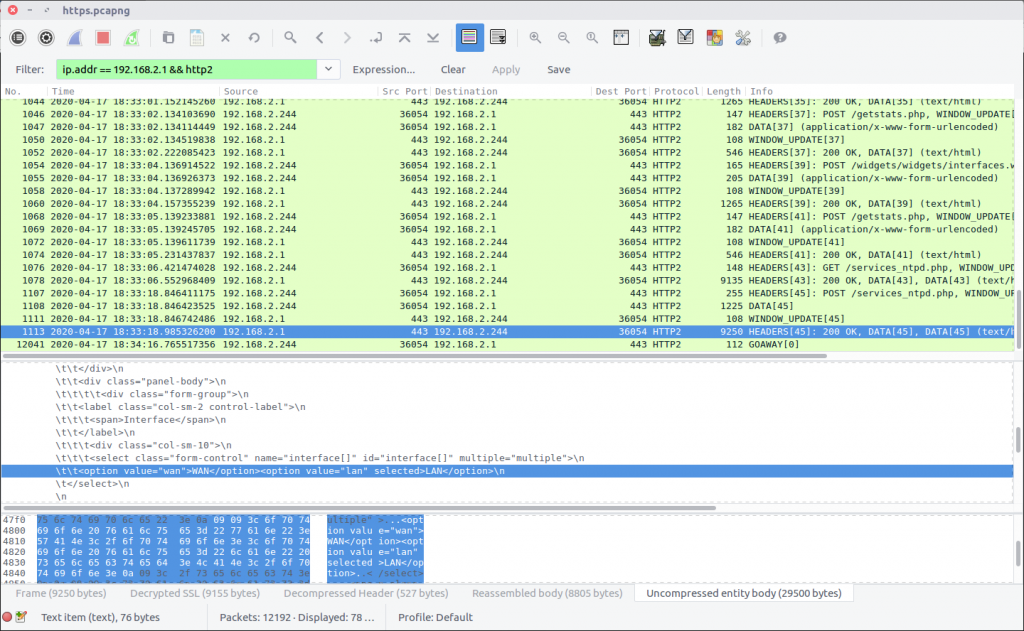
I had assumed that I would be able to identify the service being assigned to the interface by examining POST requests, as per Question 4. Instead, after failing to find any neat and tidy POST requests, I resorted to guesswork and manual review of the HTML returned in Frame #1113. The HTML was returned in response to a request for the services_ntpd.php page and contained multiple references to NTP, so I guessed that NTP was the service in question. The HTML body contained references to the WAN and LAN interfaces, and specified that the LAN option was selected:
\t\t<option value="wan">WAN</option><option value="lan" selected>LAN</option>\n
Arrange these into the format requested, and we have our final flag:
flag<LAN:NTP>

4 thoughts on “DFA/CCSC Spring 2020 CTF – Wireshark – https.pcapng Write-up”