We have got informed that a hacker managed to get into our internal network after pivoting through the web platform that runs in public internet. He managed to bypass our small product stocks logging platform and then he got our costumer database file. We believe that only one of our costumers was targeted. Can you find out who the customer was?
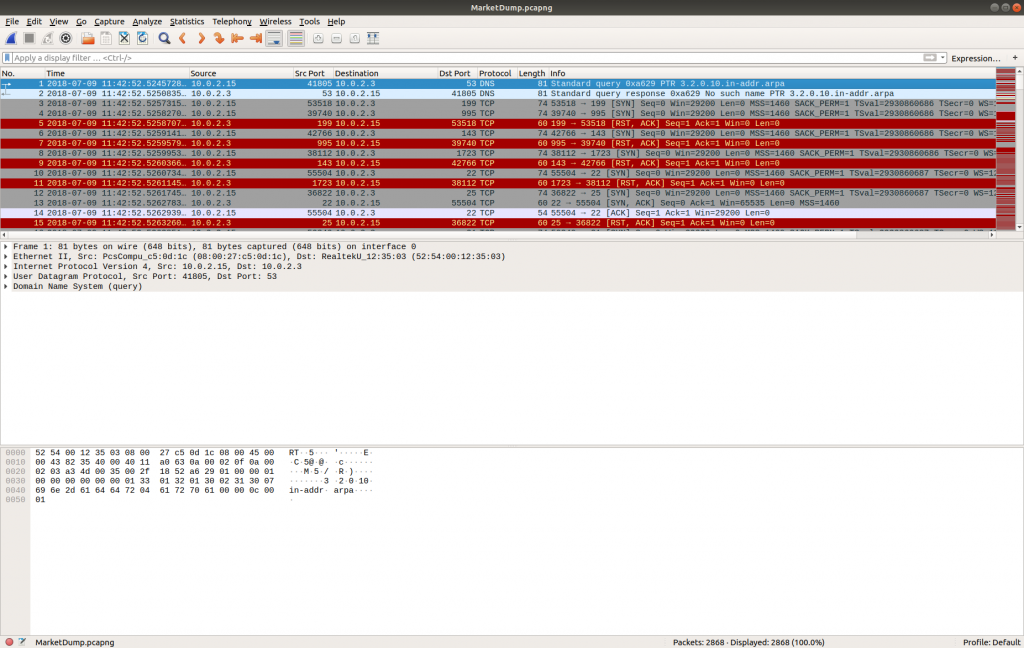
This time all that is provided is a PCAP file; I started by opening it up in Wireshark…
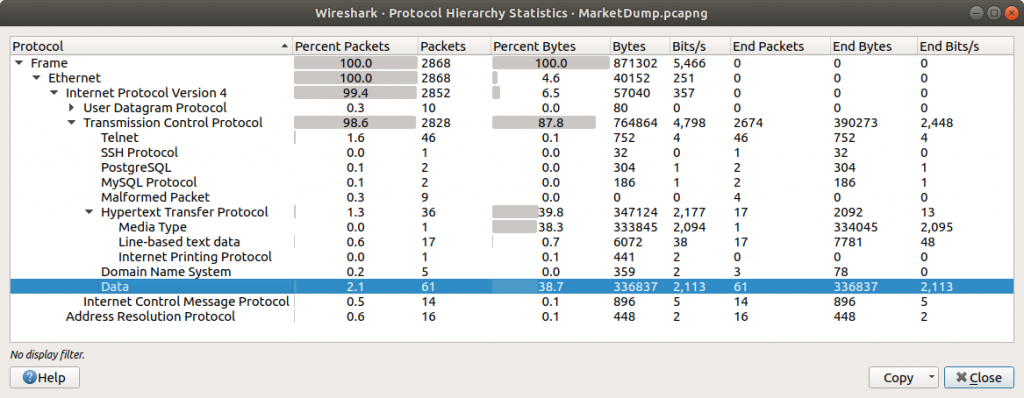
…and viewing the Protocol Hierarchy Statistics.
The statistics report that 38.7% of the TCP bytes are simply Data – that seems an interesting enough starting point. I used a simple Display Filter:
data
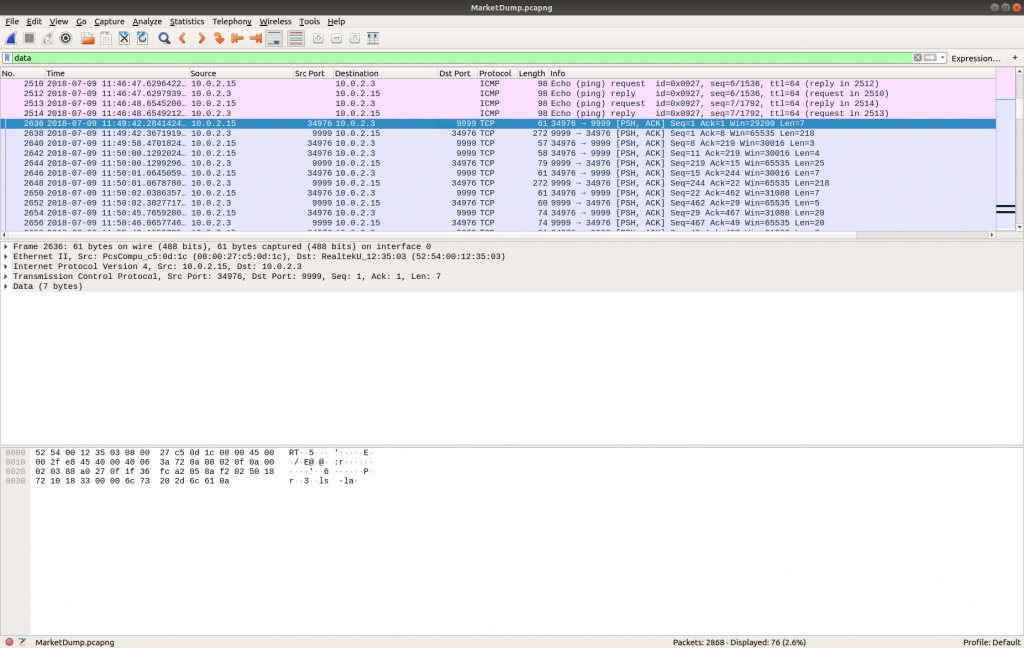
Then selected the first of the TCP packets (#2636) and Follow TCP Stream (TCP Stream #1056) to allow me to follow the session more easily.
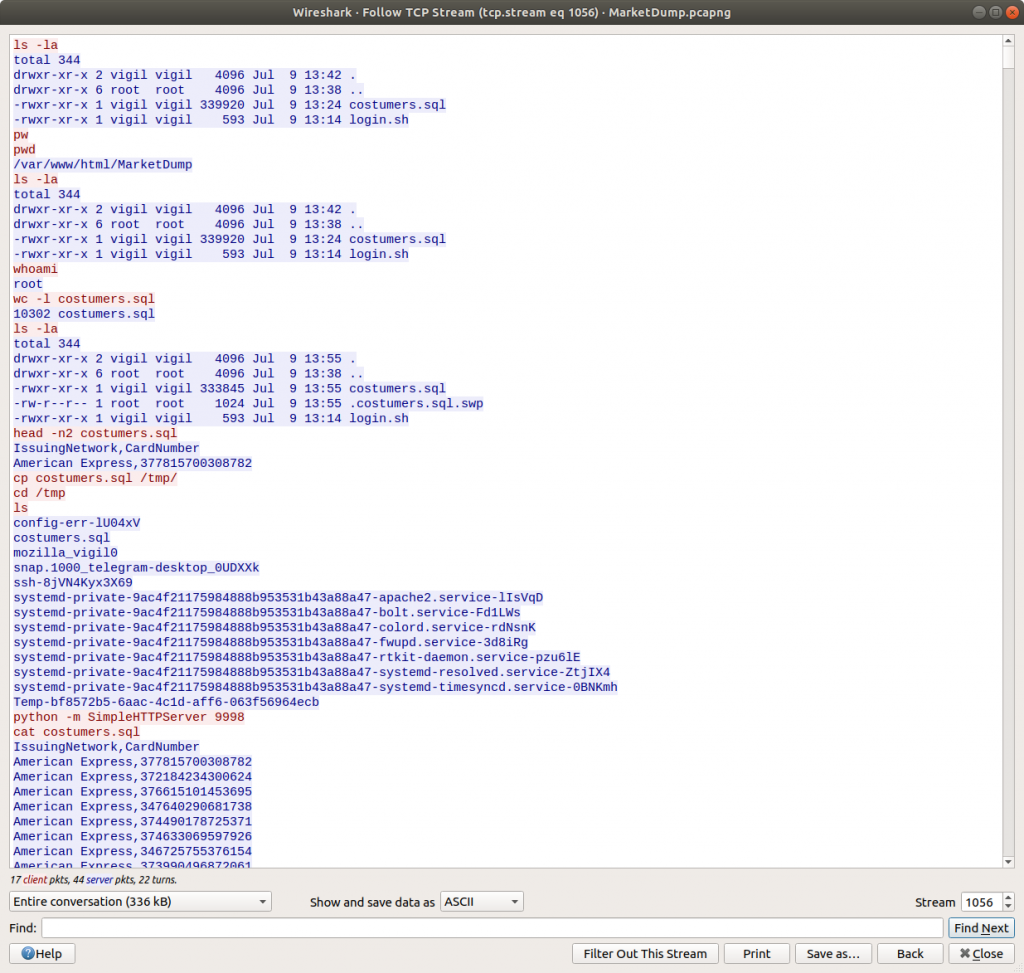
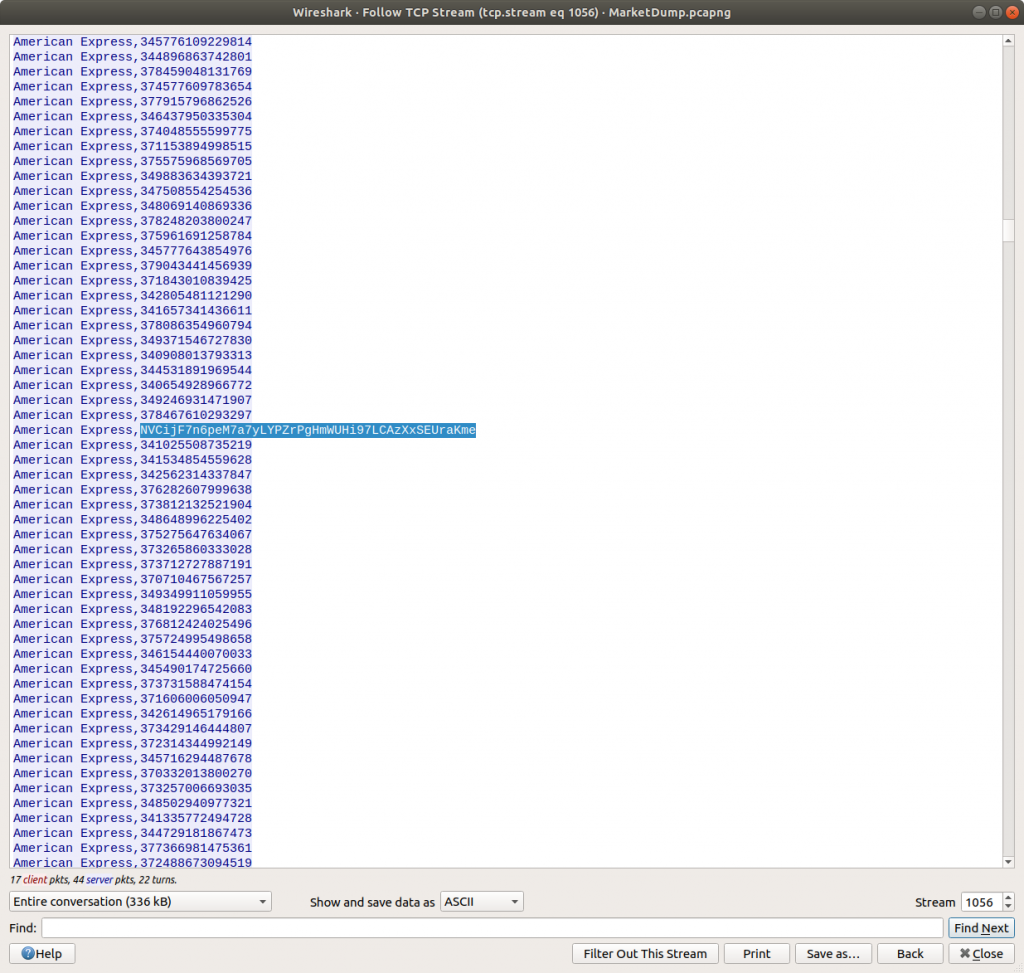
It looks like we have a capture of all the commands the attacker ran on the host post-compromise, including a dump of a text file – costumers.sql
cat costumers.sql
Scrolling through the dumped file it becomes apparent that one of the lines stands out.
American Express, NVCijF7n6peM7a7yLYPZrPgHmWUHi97LCAzXxSEUraKme
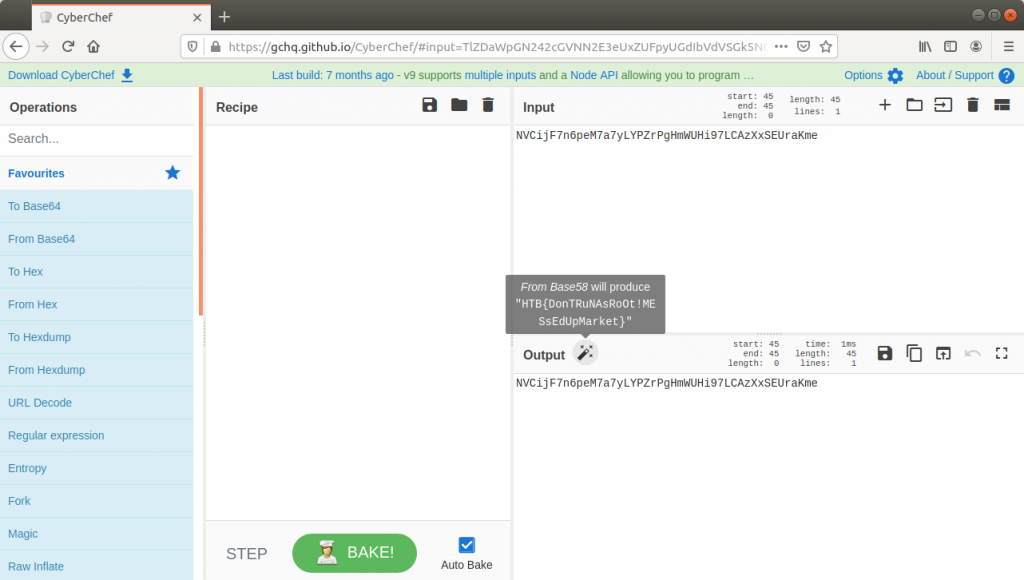
It kind of looks like base64, but the character set is not quite right. CyberChef should help make sense of this.
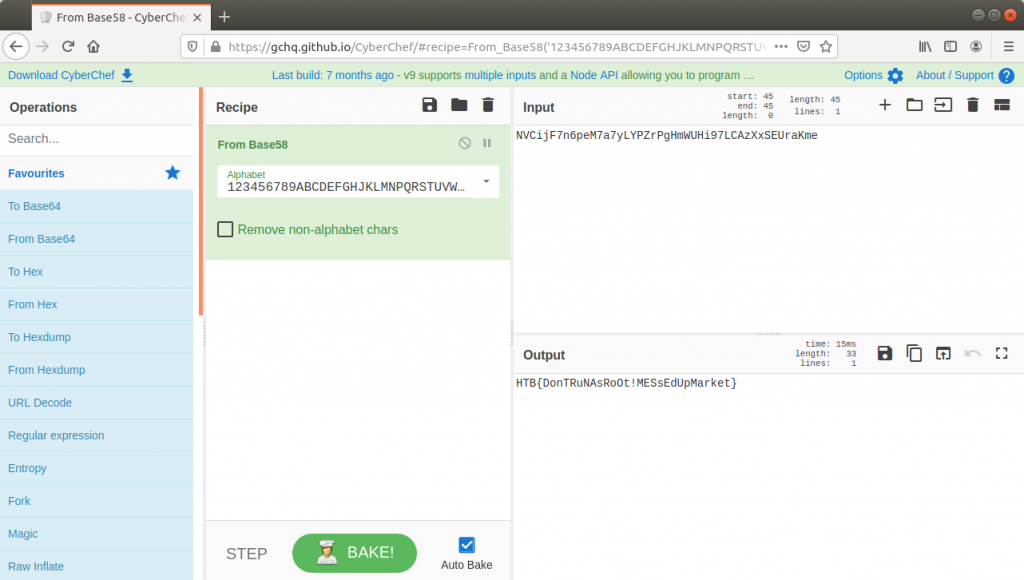
One of the really helpful things about CyberChef is that sometimes it just knows what the data is. The magic function suggests the data is actually base58 encoded…
…and there we go. Flag retrieved and challenge solved!
Flag
HTB{DonTRuNAsRoOt!MESsEdUpMarket}
1 thoughts on “Hack The Box – MarketDump (Forensics Challenge)”