OtterCTF dates from December 2018 and includes reverse engineering, steganography, network traffic, and more traditional forensics challenges. This write-up covers the network forensics portion. I have previously written-up the memory forensics section, and the Birdman’s Data and Look At Me network challenges. The whole CTF is available to play as of the publication of this post.
I managed to complete three of the four challenges in the network traffic section of the CTF. This post is a write-up of the Otter Leak challenge.
We start off by downloading the PCAP. The MD5 and SHA1 hashes are:
MD5: d0ab559c54fffe713fd13e9b0f7174df SHA1: 35a934a665497c111ad572299840f002476cff81
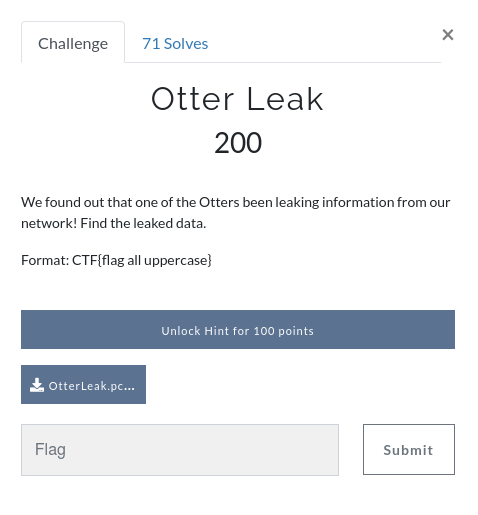
Opening the PCAP file with Wireshark, we can check the Protocol Hierarchy to get a quick summary of the kind of traffic we are working with.
We can see some SSH traffic, but more interesting at the moment is the SMBv2 traffic which is often used to transfer files. We could use a tool like Network Miner to extract any file objects from the PCAP, but Wireshark gives us the means to do this as well.
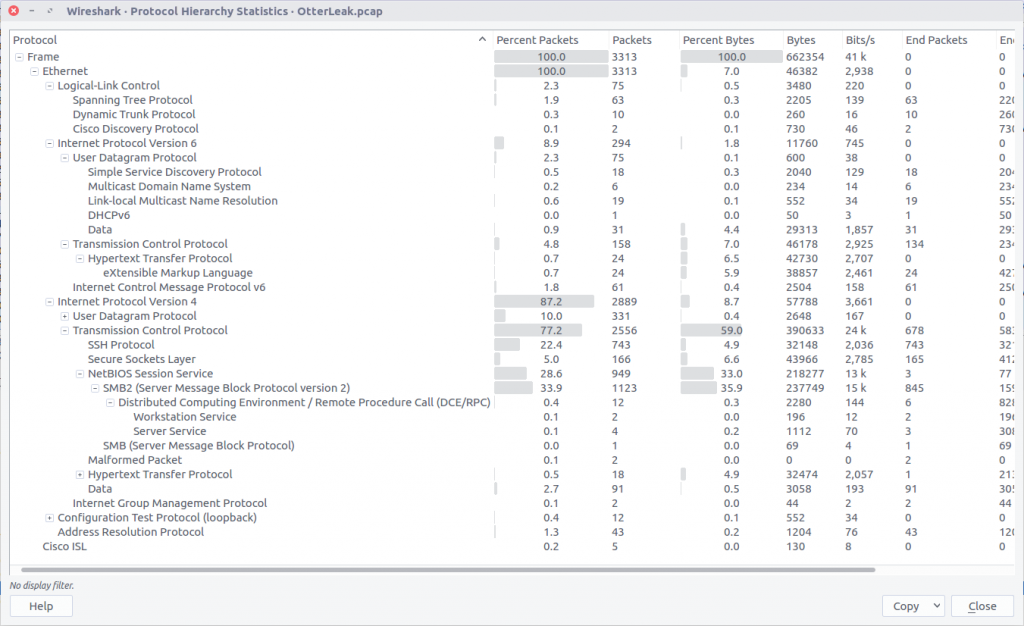
Checking the Export SMB Objects window, we can see a large number of files with names suggesting they are images, but with a file size of only 1 byte. Let’s export them all to a new directory and see what we have.
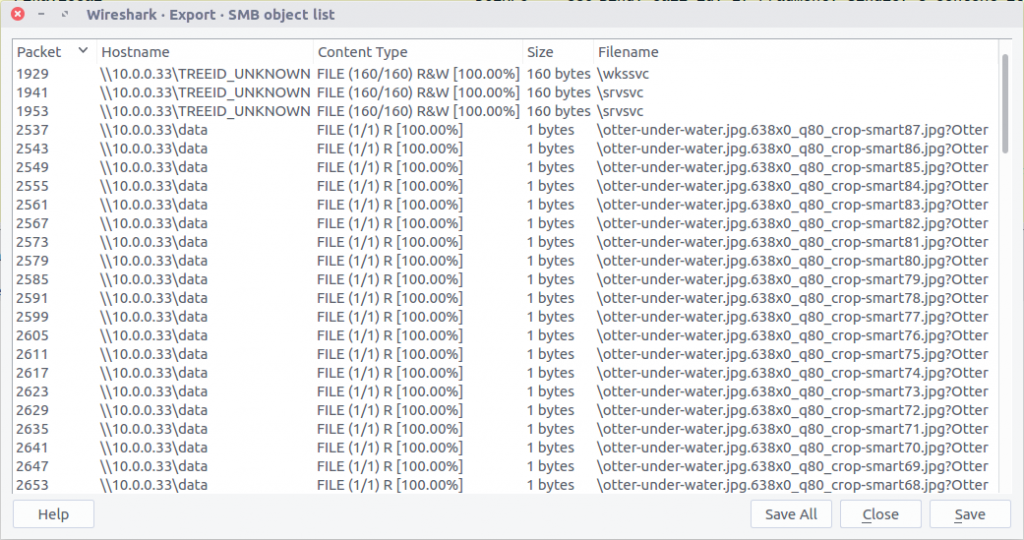
We can use the cat command to print the content of all our 1-byte files to the terminal…
cat export/%5cotter-under-water.jpg.638x0_q80_crop-smart*
…giving us the following output:
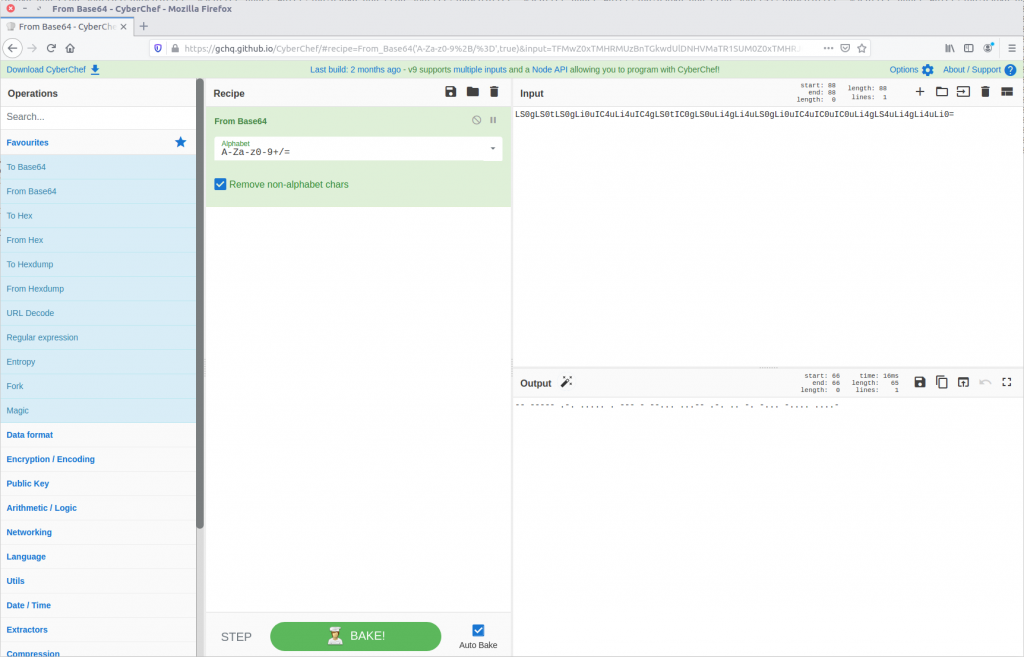
LS0gLS0tLS0gLi0uIC4uLi4uIC4gLS0tIC0gLS0uLi4gLi4uLS0gLi0uIC4uIC0uIC0uLi4gLS4uLi4gLi4uLi0=
Our output has the = padding suggesting we might be dealing with base64 encoding. Let’s see what CyberChef makes of this.
Running the From Base64 operation gives us something that looks like Morse Code.
-- ----- .-. ..... . --- - --... ...-- .-. .. -. -... -.... ....-
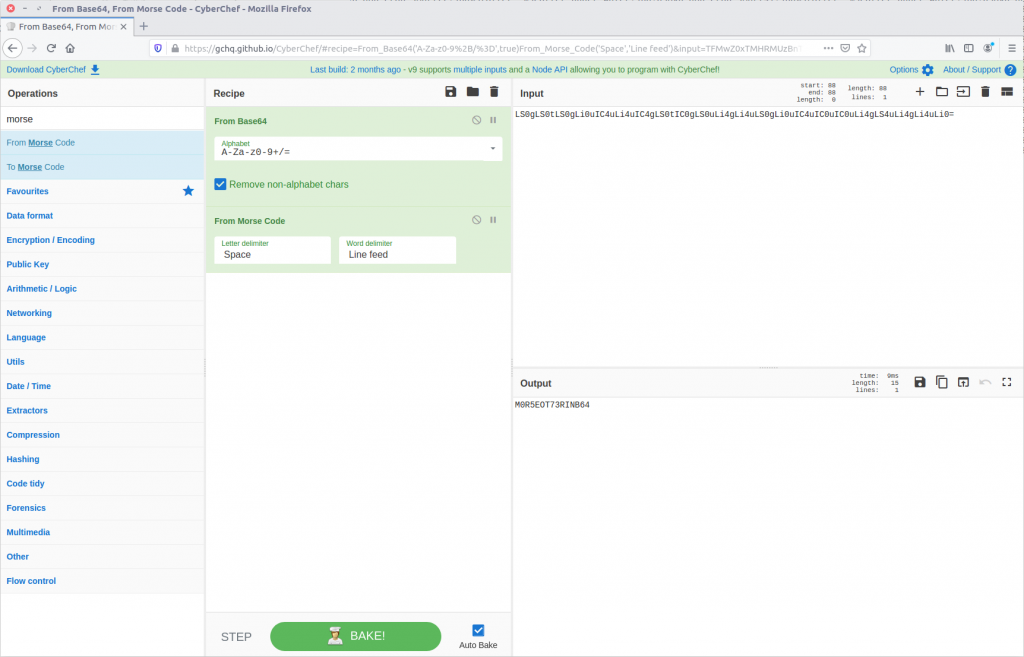
We could try to decipher this by hand, or we can use CyberChef’s From Morse Code operation to do it for us.
And just like, out pops our plaintext leaked data and our flag.
CTF{M0R5EOT73RINB64}

1 thoughts on “OtterCTF 2018 – Network Challenges – Otter Leak Write-up”